October 21, 2025
.png)
The walls are up, the wiring’s in, and it’s finally time for inspection day. The Verification & Validation (V&V) Phase is when the inspector walks through your cybersecurity house - checking that every outlet works, every circuit is grounded, and every lock does its job.
In product terms, this is where security controls, requirements, and documentation are tested, verified, and validated - the formal evidence that your device was built securely, performs as intended, and can withstand the threats it was designed to resist.
The Concept and Design phases defined what and how to build. Now comes the moment to prove it all works.
Just like a building inspection, V&V doesn’t happen all at once. Some tests are run early, as individual systems come online; others wait until everything is integrated. The goal is simple: make sure every requirement, from encryption to authentication to patching, performs exactly as promised - safely, securely, and reliably.
The JSP breaks this phase into three key inspection checkpoints:
Together, they form the final inspection - a blend of craftsmanship review and stress test before the keys are handed over.
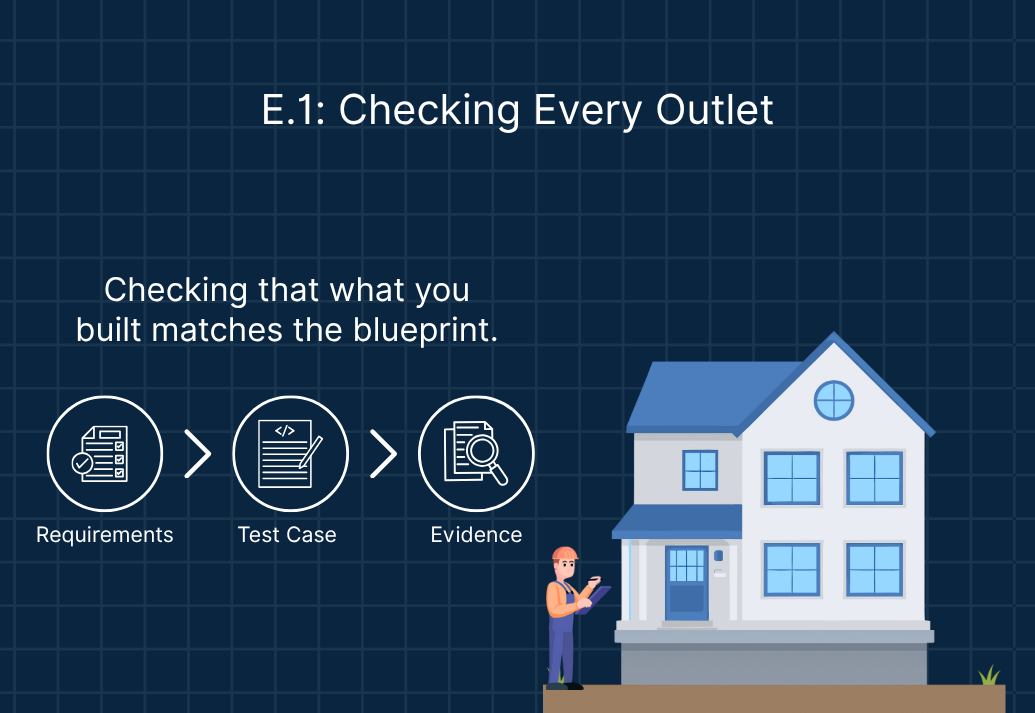
This is the first pass of the inspection - confirming that every switch, outlet, and smoke detector was installed where the blueprint said it should be.
In device terms, that means ensuring security requirements are verified through traceable test cases. Unit and integration tests are designed to confirm that encryption works as implemented, access controls function properly, and data is logged as required.
The best inspectors don’t rely on guesswork - they follow a checklist. Each test is tied to a specific requirement and documented so it can be repeated later. Some tests are automated (run continuously through regression suites), while others require careful manual validation.
When this pass is complete, you have the evidence that what you built actually matches the blueprint - no missing locks, no dead circuits, no undocumented shortcuts.
Even the best-built homes need to be checked for hidden cracks or faulty wiring. In cybersecurity, that means identifying known vulnerabilities using automated scanning tools and regularly updated databases like the NVD and CISA’s Known Exploited Vulnerability list.
These scans reveal whether any third-party components have reported flaws or misconfigurations - the equivalent of finding a recalled breaker or a leaking pipe. But a mature inspection doesn’t stop at detection; it evaluates context and exposure. A vulnerability in one product might not pose the same risk in another, depending on how it’s used or isolated.
By analyzing these findings through the lens of exploitability and impact, your team can distinguish between what needs urgent repair and what simply needs monitoring - ensuring the house passes not just today’s inspection, but tomorrow’s as well.

Once the cosmetic inspection is complete, it’s time for the real test - slam the doors, crank the system, and see if anything breaks. This is where penetration testing, robustness testing, and resiliency testing come in.
Penetration testing simulates an intruder’s attempt to bypass your locks - probing for weak points in authentication, data flows, and configurations. The best pen tests combine technical precision with creativity, chaining small issues into meaningful risks, much like testing how a door, window, and vent might together create an entry point.
Robustness testing takes a broader approach, running standardized test suites to ensure each subsystem can withstand a range of known attacks. Resiliency testing pushes the system past its limits - like simulating a storm - to confirm that even if something fails, the device recovers gracefully without compromising patient safety or data integrity.
When done correctly, these tests don’t just validate your defenses; they demonstrate how well the house holds up when the unexpected happens.

Inspection day always draws a crowd - and for good reason. QA and Engineering are the first ones on site, running through their punch list to verify that every outlet works, every lock turns, and every item on the software bill of material (SBOM) is up to date. RA/QA follows close behind, clipboard in hand, documenting test results and making sure every security control can be traced back to its blueprint. Product Managers keep everyone on schedule, tracking open issues and confirming that nothing gets left unfinished before the sign-off. Clinicians and usability teams walk through the space too, making sure the added security features don’t make the “house” harder or less safe to live in. And then there are the independent inspectors - penetration testers and outside reviewers - the fresh set of eyes who double-check the craftsmanship and make sure the final build meets every code and safety requirement.
Verification & Validation is where talk becomes proof. Regulators will expect to see traceability between requirements, controls, and tests - evidence that every identified risk was verified, validated, or justified. Hospitals and buyers will ask for the same proof when evaluating security posture.
If these records are missing or incomplete, it’s like failing your final inspection - you can’t move in until the issues are resolved, and every day of delay costs time, money, and trust.
When the inspector signs off, you’re not just getting approval - you’re earning confidence.
Your device now has documented evidence that:
It’s not just a stamp of compliance - it’s proof of quality craftsmanship.
The Verification & Validation Phase is the inspection of your cybersecurity house. This is where you prove that every bolt, beam, and lock was installed to spec - that your security controls hold up under pressure, your vulnerabilities are managed, and your device is ready for safe occupancy.
When builders, testers, and inspectors all work together, the outcome isn’t just a product that passes FDA review - it’s one you’d trust your own family to live in.


December 16, 2025


December 10, 2025
.png)
November 10, 2025
Get the latest healthcare cybersecurity news right in your inbox.
We'll never spam you or sell your information

