October 13, 2025
.png)
If the Concept Phase poured the foundation, Design & Development is when your cybersecurity house begins to take shape. Walls rise, wiring is routed, and the structure starts to resemble the finished home you envisioned. At this point, every choice - where you place a wall, how you route a cable, which materials you trust - will define not only how strong the house is, but how maintainable and secure it will be for years to come.
This is the moment when intent becomes implementation. You’re no longer talking about “building securely” - you’re doing it.
The foundation has cured, the plans are approved, and the crew is on site. This is where the abstract plans of the Concept Phase become tangible. In medical device terms, this is where design inputs evolve into design outputs - the specifications, code, and documentation that prove your product was “secure by design,” not by accident.
To build security into every beam and wire, the Joint Security Plan’s (JSP’s) Design & Development Phase (Section D) walks teams through five core activities - translating requirements into reality, designing with defense in mind, validating as you build, planning for maintenance, and preparing for handoff.
It’s a progression that mirrors how a real house gets built: first you mark where the walls go, then you plan the wiring, test every system, plan for future repairs, and finally hand over the keys.
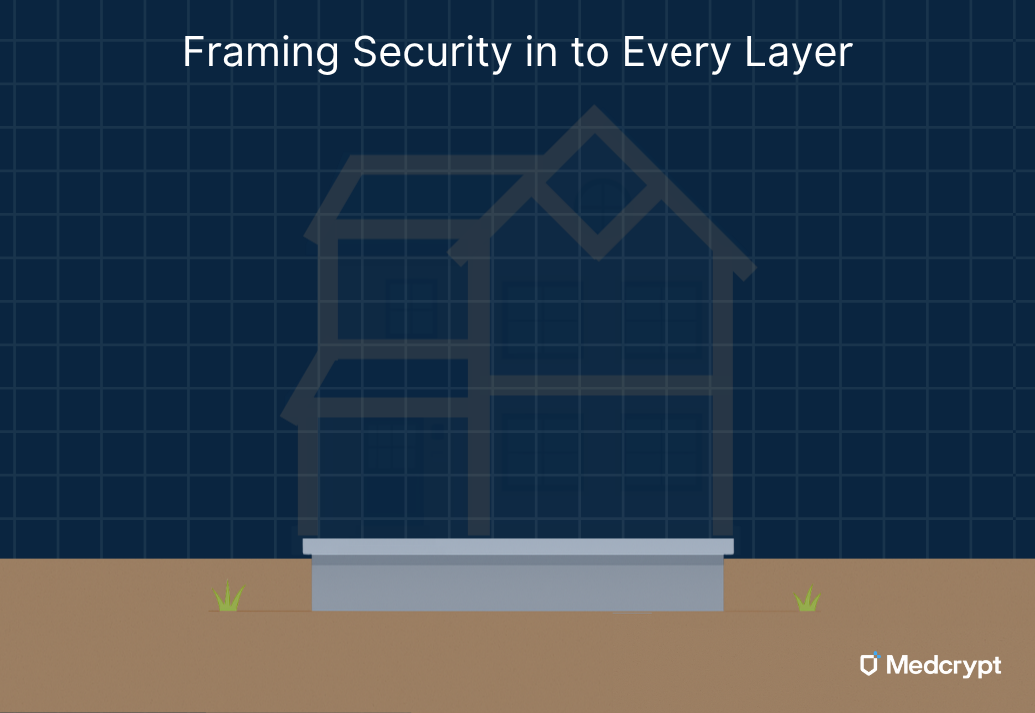
Before anyone picks up a hammer, the foreman walks the site, marking where each wall, window, and outlet belongs. In product terms, this is your security requirements development - converting big-picture needs (“this house must be safe”) into specific, testable instructions that engineers can follow.
Here, product managers, engineers, and security SMEs collaborate to turn stakeholder and regulatory expectations into detailed blueprints. Each security control - authentication, encryption, audit logging, update management, system hardening - gets a “place” in the structure, is tagged and reviewed to make sure it’s appropriate for the environment and can be verified later.
Like marking every stud and outlet before framing, this step keeps the team aligned. By the time the first boards go up, everyone knows what belongs where - and nothing important gets forgotten behind the walls.
.jpg)
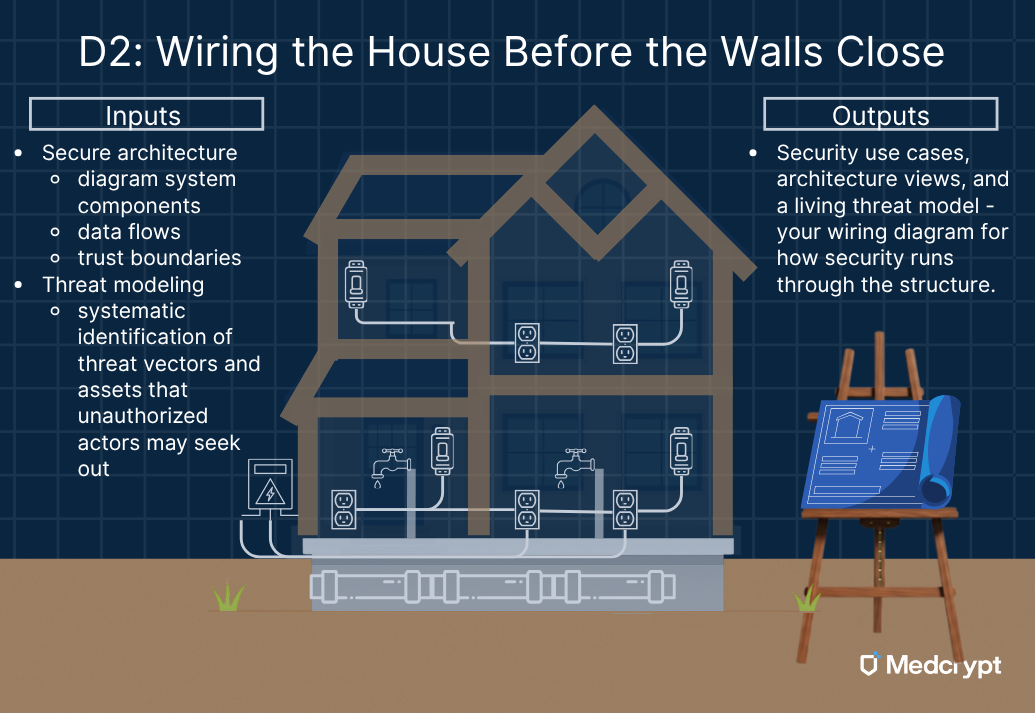
Once the frame is outlined, you start running wire and plumbing through it - a delicate stage that defines how power, water, and data will flow. The same applies to your device architecture.
Threat modeling is your version of the electrical diagram: it maps every path through which a current (or data) might flow, helping you identify overloads, leaks, or weak points before they become expensive problems. Architects and engineers work together to diagram system components, data flows, and trust boundaries - like separating the electrical from the water lines - and to specify the security controls that keep each subsystem isolated and safe.
As these models evolve, the design documentation becomes the house’s wiring map - something inspectors, auditors, and even new team members can rely on later to understand how everything fits together. It’s not just a drawing, it’s the backbone of your home’s security system.
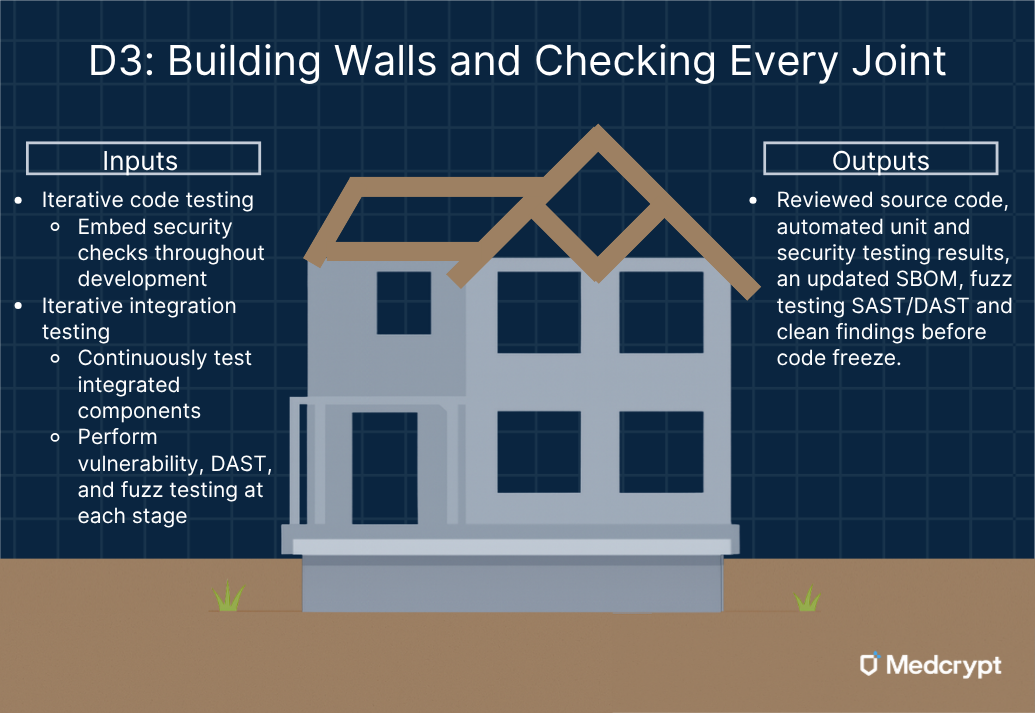
Now the house really starts to look like a house. Framing is complete, walls are being filled in, and the work becomes visible - but every nail, screw, and seam still needs inspection.
For developers, this means writing code under secure coding standards, running static analysis tools with every check-in, and performing code reviews to make sure nothing unsafe gets sealed behind drywall. Each piece of code is like a new section of wall: it must line up precisely with the structure and hold under pressure.
As rooms come together, integration testing ensures that the different systems - HVAC, electrical, plumbing - all work together safely. The digital equivalent includes dynamic testing, fuzzing, and host scans to find vulnerabilities early.
The software bill of materials (SBOM), is continuously updated as components are added, acts as your inventory list - every material logged, every supplier verified. By the time you reach the inspection, you know exactly what’s inside your walls.
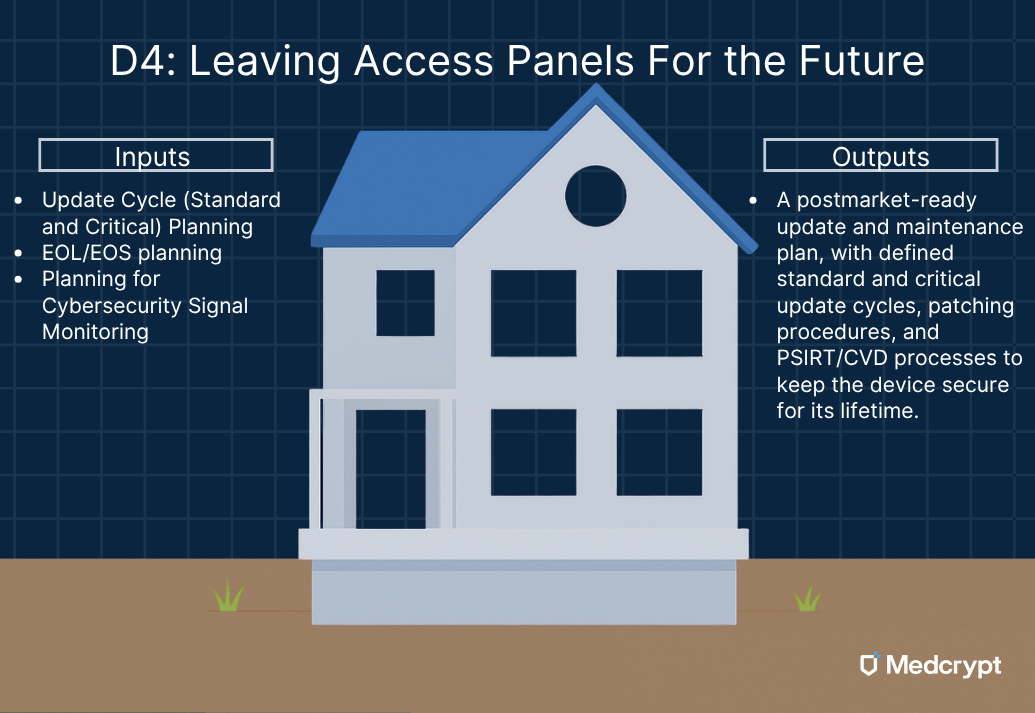
Good builders plan for maintenance. They know that one day, someone will need to reach the pipes behind that wall or replace an electrical breaker. Cybersecurity is no different - it’s about designing for change.
During development, teams define how updates will happen: which changes can occur on a standard cycle, which require a critical out-of-cycle patch, and how to apply them safely without interrupting essential performance. Update mechanisms are tested for security - code signing, rollback procedures, and access control - just as you’d test an emergency shutoff before closing the wall.
Every home needs a maintenance plan, and every medical device does too. Designing with updates in mind ensures that when a vulnerability is discovered years later, you can fix it cleanly, not demolish half the structure to reach it.
At last, the house stands tall. Walls are painted, lights work, and it’s time for the walkthrough before handing over the keys. This is the secure transfer to manufacturing - the point where you confirm everything matches the plans and the house can be safely replicated.
All design documentation, architecture diagrams, and code are reviewed to confirm completeness and integrity. Builds are signed and version-controlled, ensuring the production team always works from the approved design. Keys and credentials are handled with care, like passing the home’s master keys from builder to owner.
Before the transfer, the manufacturer prepares a security binder for the “homeowner” - the customer and regulator - that includes the SBOM, patch plan, access methods, EOL/EOS timelines, and guidance for secure operation. It’s the owner’s manual that ensures the house can be maintained long after move-in.
Framers can’t build without electricians, and plumbers can’t work without the plans. In the Design & Development phase, engineers, architects, product managers, and security experts all need to coordinate daily. RA/QA ensures traceability, security teams monitor the integrity of requirements and code, and executives sign off on resources and accepted risks. It’s a synchronized build site - every trade working from the same blueprint.
The Design & Development phase is where “secure by design” becomes visible. Regulators, auditors, and customers won’t take your word for it - they’ll look at your wiring diagrams (architecture), test reports (SAST/DAST), and maintenance plans (updates, patching, and EOL/EOS).
If you skip inspections here, the cracks won’t appear until much later - when fixing them is ten times harder.
When you step back and look at the finished structure, you’ll see more than walls and wiring - you’ll see proof that everything inside was built with care, traceability, and intention.
Your product now has:
You’ve built a system designed to last - a cybersecurity house with straight walls, reliable wiring, and all the access panels you’ll ever need.
The Design & Development phase is where your cybersecurity framework becomes reality. It’s the framing, wiring, and finishing of your secure-by-design house - the point where structure meets function and where every decision is visible in the final build.
When each trade shows up - engineers, testers, regulatory leads, and security architects - the result is a product that’s not just functional but fortified. Do it well, and the next phase, Verification & Validation, becomes less about finding cracks and more about confirming craftsmanship.
Because when the inspector shows up - whether it’s the FDA, a hospital buyer, or your own audit team - they won’t just see a compliant product. They’ll see one that was built securely, thoughtfully, and to code from the very first nail.


December 16, 2025


December 10, 2025
.png)
November 10, 2025
Get the latest healthcare cybersecurity news right in your inbox.
We'll never spam you or sell your information

