September 30, 2025
.jpg)
When people hear “cybersecurity,” most assume it’s someone else’s problem - usually IT’s job, or maybe RA/QA’s headache when FDA submission time comes. This is true for traditional IT security and is certainly also true for product security, yet that thinking is exactly what derails projects, delays approvals, and frustrates customers.
The truth is, cybersecurity is cross-functional. It’s not just about engineers writing secure code or security experts running pen tests. Product managers, QA, regulatory, executives even service and marketing teams all play a role. And that’s why the Health Sector Coordinating Council (HSCC) created the Joint Security Plan (JSP): a framework that shows how medical device manufacturers can align people, processes, and evidence across the entire product lifecycle.
At Medcrypt we view the JSP as the architectural plan for your cybersecurity house. It isn’t extra work; it’s the organizing blue print that makes sure every part of the house is built soundly. Early choices form the foundation. Requirements, secure coding, and cryptography decisions become the framing. Verification and validation serve as the inspection. And once the product is in market, monitoring, disclosure, and patching are the long-term maintenance that keeps it safe.
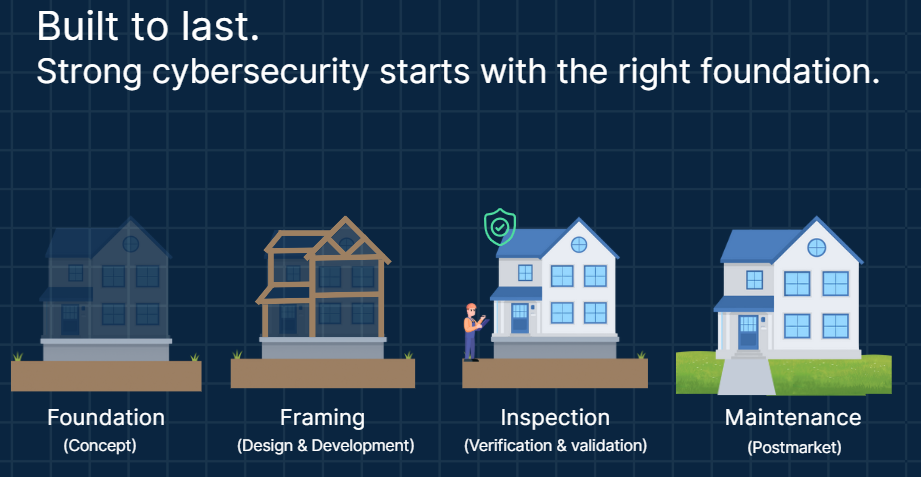
Every role contributes differently to keeping that house standing. Builders - product managers, engineers, RA/QA - bake security into design controls, code, and testing. Explainers - sales, marketing, service, even legal - carry the story forward with customers and regulators. Owners - executives and incident response - align resources and priorities with business risk. If any group assumes “ someone else is handling it,” cracks form in the structure.
Here’s where things often break down: evidence. FDA reviewers expect clear traceability from requirements to risk, from implemented control to test results, all backed by documented evidence. Hospitals increasingly ask for security artifacts like SBOMs and MDS2 forms. And market reputation depends on demonstrating cryptography decision or update strategy doesn’t just delay submissions; it can trigger redesigns that cost hundreds of thousands of dollars in rework.
That’s why the JSP matters. It’s not just a framework on paper - it’s a way to coordinate, to show “who does what, when, and why,” and to make sure your cybersecurity story holds up under regulatory and customer scrutiny.
Over the next four weeks, we’ll break down each phase of the JSP in more detail, starting with laying the foundation in the Concept phase and ending with how to maintain security postmarket.


December 16, 2025


December 10, 2025
.png)
November 10, 2025
Get the latest healthcare cybersecurity news right in your inbox.
We'll never spam you or sell your information

