
September 17, 2025

A new report from Infosecurity Magazine sheds light on a troubling disconnect between security teams and business stakeholders:
These findings echo what we see in the medical device industry: security is often approached as an afterthought or a mere compliance checkbox, rather than a driver of sustainable business performance - fueling customer trust, protecting intellectual property (IP), and contributing to both long-term strategic positioning and near-term revenue growth.
The truth is, when security is properly embedded into product design and lifecycle planning from the earliest stages, it’s not a drag on innovation - it’s a launchpad for it.
Let’s put the business case into numbers.
Scenario A: Secure, Over-the-Air (OTA) Updates
You invest upfront in secure OTA infrastructure, ensuring devices can receive routine and emergency updates remotely, with strong security and trust through well-designed authentication and encryption. Updates can be delivered in hours, across thousands of devices, without rolling a single truck. You can confirm the rollout remotely to monitor completeness and track metrics.
Scenario B: Manual Field Updates
You send a fleet of maintenance technicians - in their Priuses, USB drives in hand - to manually update every device in the field. (Thanks to Brian Fitzgerald for the persistent visual of the Prius fleet - still iconic!). Each visit requires travel, time, chain-of-custody controls, and customer downtime as well as poses the risk of USB-introduced malware. Multiply that by hundreds or thousands of devices.
Scenario C: Replace Devices Entirely
If your devices can’t be updated securely at all, your only option may be replacement - at full manufacturing, shipping, and installation cost - every time a critical vulnerability or feature update is needed.
Example Scenario
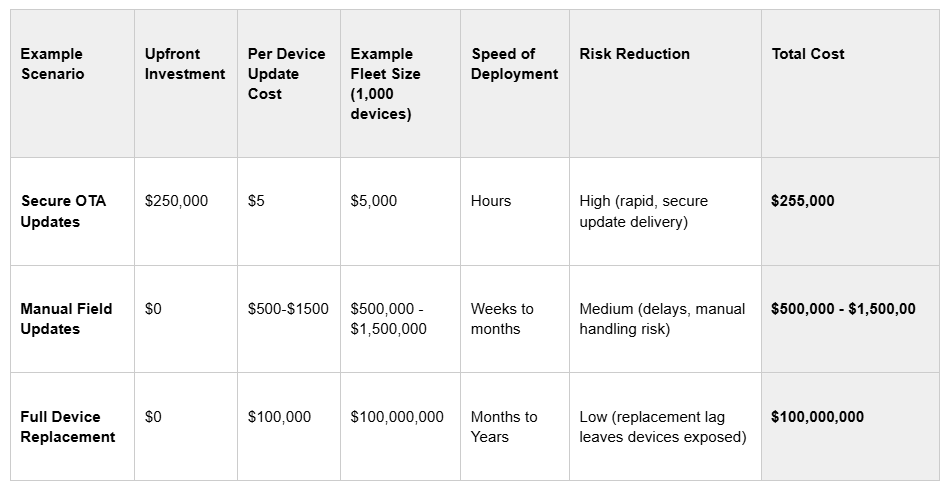
And this math doesn’t even account for emergency patches triggered by critical vulnerabilities like Heartbleed (OpenSSL), URGENT 11 ( VxWorks), or Sweyntooth (various BLE), which require immediate action to avoid patient safety risks, operational disruptions, and regulatory penalties.
Achieving reliable and proven (i.e., well-documented) security requires mature engineering and lifecycle management processes. Secure OTA updates, automated patching, and rapid vulnerability response are only possible when the underlying technical and regulatory frameworks are in place.
However, many MDMs struggle to build the required maturity across their organization. They may lack a clear framework for measuring security posture, struggle to align technical teams with regulatory expectations, or find it difficult to identify and prioritize areas for improvement.
That’s where the Product Security Intelligence Platform (PSIP) comes in. PSIP gives MDMs a clear, data-driven view of security maturity across their product portfolio. With PSIP, you can:
Instead of treating security as an afterthought, PSIP helps organizations embed it into every stage of the product lifecycle - turning security into a genuine growth driver.
Bottom line:
Security isn’t just about preventing breaches - it’s about developing processes and building products that are secure, efficient, and trusted. The numbers speak for themselves: secure by design doesn’t just reduce risk - it reduces cost, speeds innovation, and fuels business growth.


December 16, 2025


December 10, 2025
.png)
November 10, 2025
Get the latest healthcare cybersecurity news right in your inbox.
We'll never spam you or sell your information

