
July 16, 2025

In our first blog, we introduced post-quantum cryptography (PQC) and why long-lived connected medical devices are uniquely vulnerable to emerging threats from quantum computing.
In this post, we’ll dig deeper into the regulatory perspective - and explain how cryptographic flexibility and planning for future standards align with current FDA cybersecurity expectations.
The FDA’s 2023 Premarket Cybersecurity Guidance outlines the need for medical devices to be secure by design - with protections that remain effective throughout the device’s full lifecycle.
Core expectations include:
These expectations are reinforced in Section 524B of the FD&C Act, which requires that submissions for certain cyber devices include “reasonable assurance” that protections will remain effective in the face of evolving threats.
While the FDA does not currently require use of post-quantum algorithms, it does expect device makers to:
This is where crypto-agility becomes essential.
Crypto-agility is the ability to change or upgrade cryptographic algorithms without redesigning the entire device or disrupting its secure functionality.
The 2023 guidance (Section VI.A) calls for manufacturers to describe how cryptography is used to implement confidentiality, integrity, and authentication in:
While the FDA doesn’t mandate a “cryptographic inventory,” many device makers are using Cryptographic Bills of Materials (CBOMs) - internal tools to track:
CBOMs are not required but are increasingly viewed as a best practice to support submission clarity and audit readiness.
FDA guidance expects devices to support secure updates over time - including the ability to:
This requirement aligns directly with PQC planning, as legacy crypto (like RSA and ECC) will eventually need to be phased out in favor of quantum-resistant algorithms.
The FDA expects a system-level approach to cybersecurity. Your documentation should show:
This is not about predicting the future - it's about showing that your architecture is flexible enough to adapt when change comes.
Devices already in the field present a serious challenge. Many were not designed for cryptographic updates and may:
For these products, the FDA expects risk-based mitigation strategies, such as:
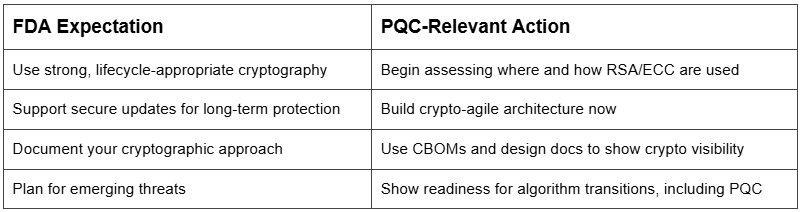
You don’t need to implement PQC today - but you do need to plan for change. Regulators want to see that your devices can adapt to the evolving threat landscape, including the eventual shift to quantum-safe standards.
Up Next: Why Preparing for Cryptographic Change Requires More Than a Firmware Update
We’ll explore what crypto-agility really means for medical device architecture - and why secure update mechanisms are just the starting point.

March 4, 2026

February 27, 2026


December 16, 2025
Get the latest healthcare cybersecurity news right in your inbox.
We'll never spam you or sell your information

